Windows Professional 5. Find all those strings in config files. This will work fine for a gui session. This occurs because windows will try, for every white space, to find the binary in every intermediate folder. In March Microsoft stopped maintaining the security bulletin search. We could place our payload with any of the following paths: CVE MS - Vulnerabilities exist when Microsoft Edge improperly accesses objects in memory - allows remote code execution.
| Uploader: | Tygoramar |
| Date Added: | 25 July 2015 |
| File Size: | 55.1 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 37408 |
| Price: | Free* [*Free Regsitration Required] |
Module Name
Obtain the path of the executable called by a Windows service good for checking Unquoted Paths: Uses DES but the key space is small only uppercase, not salted, 14 chars or padded to These are common files to find them in. To capture NTLM hash.
Run an arbitrary command: CVE allows an attacker to execute code when a victim opens a specially crafted file - remote code execution. Third party drivers might contain vulnerabilities, find them running: Windows Professional 5.

A top selling security ebook at Amazon. Replace the affected service with your payload and and restart the service running: If they are, create your own malicious msi: CVE MS - Vulnerabilities exist when Microsoft Edge improperly accesses objects in memory - allows remote code execution.
ms Archives | A Group of Ethical Hacker's Diary
We might even be able to override the service executable, always check md11 the permissions of the service binary: Stuff in the registry: We shamelessly use harmj0y's guide as reference point for the following guide. Permissions on a folder recursively: More info about permissions:.
Handling reverse shell using meterpreter: Automatically downloads and js11 exploit. MIC files - code execution. Once we have everything setup, the process is straight forward.
Local privilege escalation with MS11-080
If it fails because of a missing dependency, run the following: This might be useful if we need to run it in a remote shell or non-interactive web shell or such… Original Link. Replacing the affecting binary with a reverse shell or a command that creates a new user and adds it to the Administrator group.
Get exact OS version. You can automate with meterpreter: Not too long ago, I found myself in a need of escalating my privilege on a Windows box.
You get Administrator with:.
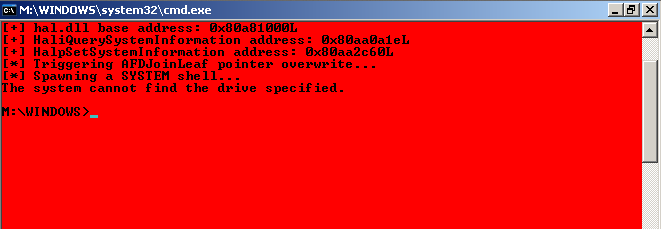
This is generally a last resort. Getting a shell in limited interpreters: Tag Archive Tag Archives for " ms ".

Generate shellcode to use within a perl exploit: This will work fine for a gui session. For example, the following path would be vulnerable: If wmic and sc is not available, you can use accesschk.
Security bulletin from MS can be found here:

No comments:
Post a Comment